Free Advice To Deciding On Credit Card Apps
Wiki Article
How Do I Check What Happens If My Credit/Debit Card Was Reported Stolen In The United States?
Follow these simple steps to determine the status of your credit card. reported as stolen from the USA. Contact your card issuer
Contact customer service at the number located on the back of the credit card.
Inform the representative that you are looking to confirm the status of your credit card, and whether it has been reported as stolen or lost.
Verification may require you to provide personal information, such as the number on your credit card and name.
Log in to your account
Log in to your online account for credit cards or for banking.
Be on the lookout for alerts or messages about your card's status.
Review the transactions that have occurred recently and identify suspicious or unauthorized activity.
Check Your Credit Report
Obtain a free copy of your credit report from each of the three major credit bureaus (Equifax, Experian, TransUnion) through AnnualCreditReport.com.
Examine the report to identify suspicious credit accounts or inquiries that could suggest fraudulent activity.
Fraud Alerts and Security Freezes-
You may want to consider placing a credit freeze or fraud alert on your report if fraud or identity theft are suspected.
A fraud notice informs creditors of the need to check your information prior to giving credit. The security freeze on the other hand is a restriction on access to your report.
Make sure to report any suspicious activity.
Monitor your credit card statements and report any fraudulent transactions or unusual activity to your credit card issuer immediately.
Report suspected identity theft and fraud to the Federal Trade Commission. Also, file a complaint with the local police department.
By contacting the credit card company, looking over account activity online, monitoring credit reports and remaining vigilant for signs of unauthorized activities You can be proactive in protecting yourself and deal with any issues that could arise from a reported fraud on your credit card.
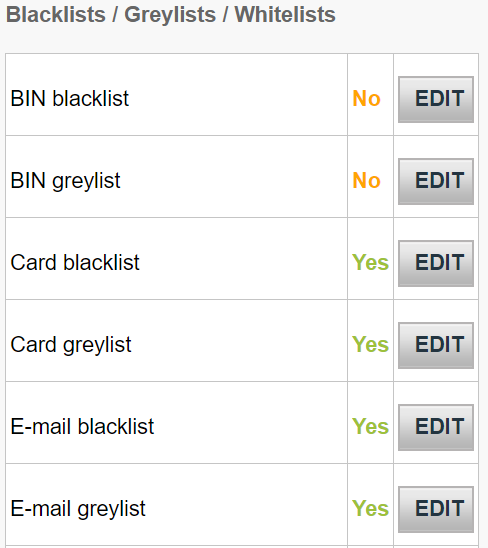
What Is My Credit Card's Status Being Blacklisted Refer To?
When a credit card is listed on blacklists, it usually refers to the credit card being identified as blocked or flagged by the card issuer or financial institution due to suspicion of fraudulent activity, security concerns, or other reasons connected to potential risks.Being on a blacklist indicates that the card may be temporarily blocked from certain transactions or usage until the problem is fixed or confirmed by the cardholder. There are a variety of reasons why a credit card could be placed on a blacklist.
Suspected Fraud - Unusual or suspicious transactions with the card that are detected as fraud could lead to the card being removed to protect the card.
Security Concerns: If there are signs of compromise (unauthorized access to data, breaches of cards, or unusual spending patterns), the card can be flagged as a security measure.
Identity Verification Issues: If the cardholder is unable to verify their identity, it can temporarily block the card. This happens when there are additional verification requirements.
Card stolen or lost If a card is reported as lost or stolen, the issuer may create a block to stop misuse of the card until replacement issued.
Suspicious Activity Identifiers- Any actions or behavior associated with the card that is suspicious, such as several declined transactions, geographic anomalies, or other unusual spending patterns, could trigger a temporary block.
If a credit card is listed, it may restrict the access of the cards or their capability to make transactions until the company that issued the credit card proves its legitimacy or satisfies any concerns about potential fraud or safety risks. The cardholder needs to contact the issuer right away to address the issue, verify transactions and address any security concerns.
Cybersecurity Experts Detect And Monitor Cyber Threats, Such As Compromised Credit Cards.
Cybersecurity experts use a variety of strategies, tools and methods to detect and track cyber-attacks, such as compromised credit card data. A few of these techniques and methods include: Threat Intelligence Gathering
Collecting information from various sources, including forums, threat intelligence feeds dark web monitoring and security advisory, to stay updated on emerging security threats and security vulnerabilities.
Network Monitoring and Intrusion Detection-
Use specialized software to monitor network traffic, and spot unusual activity and suspicious behavior that may indicate illegal access or data breach.
Vulnerability assessments and penetration testing
Regular checks are conducted to identify any weaknesses in the systems, applications or networks. Penetration tests simulate attacks to detect vulnerabilities and assess the security of an organization.
Security Information and Event Management (SIEM)--
Implementing SIEM tools that aggregate and analyze log data from different sources (such as servers, firewalls, or applications) to recognize and respond to security issues in real-time.
Behavioral Analysis
Use behavioral analysis to detect irregular patterns or variations in the user's behavior within networks or in systems. This could indicate a possible compromise.
The threat of Hunting
By analyzing logs and data from systems, you can detect threats within your organization's network.
Endpoint Security Solutions
Installing solutions for endpoint protection (such antivirus, antimalware and detection and response tools for endpoints) is a great way to protect your devices from malware.
Data Protection and encryption
Implementing encryption methods in order to secure sensitive information such as credit card numbers when it is transmitted and stored it will lower the likelihood that data breaches will occur.
Forensics and Incident Response
Implementing an incident response plan will enable you to swiftly respond to emergencies. Conducting forensic analyses to investigate security breaches and identify the impact they have on organizations and their causes.
Cybersecurity experts integrate these strategies with a thorough knowledge of changing cyber-security threats, compliance requirements and the most effective methods to identify, mitigate, and address cyber-related threats, such as those that involve compromised credit card data. Cyber-attacks can be mitigated with a combination monitoring, information on threats as well as proactive security. Read the most popular savastan0 cc dumps for more tips.
